Editor's Note. OpsRamp recently attained the Service Organization Control (SOC) 2 Type II certification. An independent auditor scrutinized our data management and operational control practices as part of the audit. This blog post explains how we cleared the SOC 2 Type II audit by ensuring the availability, confidentiality and integrity of customer data in our platform.
Gartner estimates that the SaaS delivery model for IT operations management (ITOM) software was 10% of the total market in 2014. ITOM SaaS vendors saw more than 50% growth in 2014, versus 7% for the entire ITOM software market. As more enterprises adopt SaaS, how do IT leaders balance the cost savings and value of SaaS offerings with security concerns?
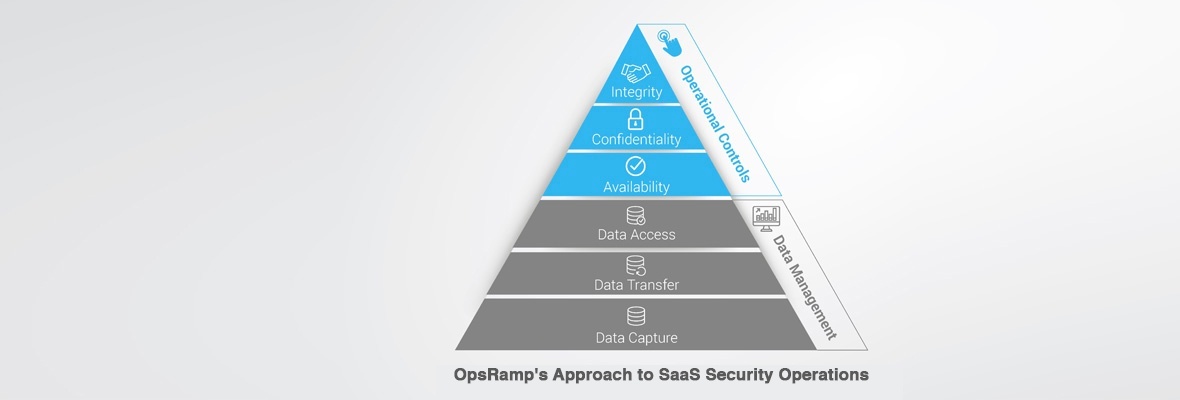
OpsRamp is a leading SaaS-based IT operations management platform that helps enterprises manage dynamic, hybrid environments. At OpsRamp, we are serious about maintaining availability, confidentiality and integrity of customer data. Our SaaS operations team uses a mix of Data Management policies (Data Capture, Data Transfer, Data Access) and Operational Control practices (Availability, Confidentiality, and Integrity) to protect data.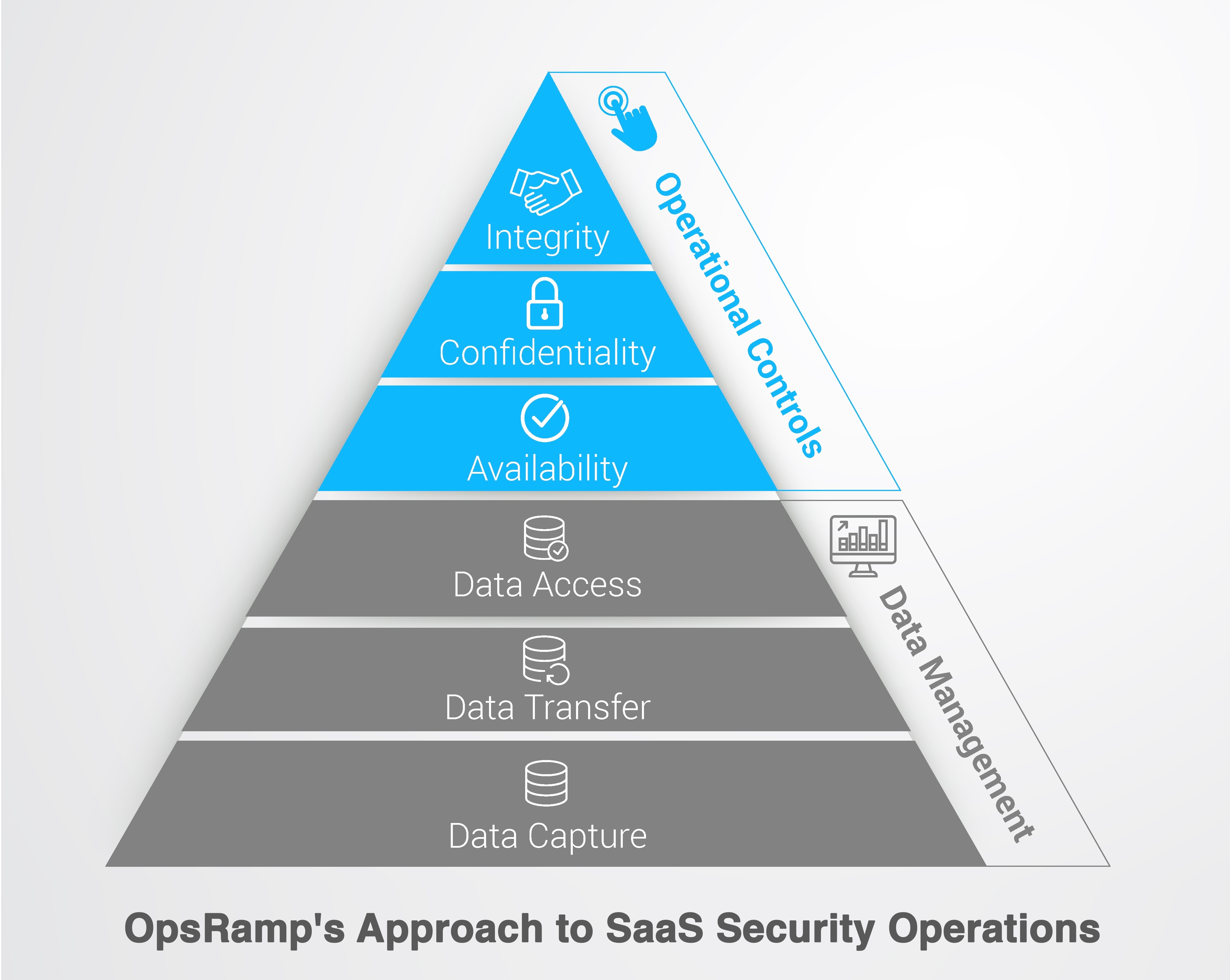
Data Management
Data Capture. OpsRamp only collects data that helps manage our customer’s IT environment.
- Performance Statistics. We collect system level information to monitor the availability and performance of managed devices.
- Events and SNMP Traps. We collect operating system events and SNMP traps to track device health.
- Device Metadata. We collect device configuration status for DNS names, models, operating systems and application configuration parameters.
- Application Performance Statistics. We collect information to track the performance of managed applications. For instance, OpsRamp understands that a customer has a Windows Server with MySQL database installed on it. OpsRamp tracks the server CPU utilization which is currently at 60%. What OpsRamp will never know is that the MySQL database stores credit card information. We don’t access data inside the application but only track performance metrics at the application layer.
Data Transfer. We logically partition and store customer data (inventory, metrics, alerts and tickets) under each tenant.
- Data Collection. OpsRamp collects data using our Gateway and Agent technologies. We encrypt all in-flight data transmitted between the OpsRamp Gateway / Agent and the OpsRamp Cloud. We eliminate man-in-the-middle attacks by establishing a secure tunnel and using key exchange so that no one can access customer data.
- Data Security. We encrypt all the data in the OpsRamp Cloud using 1024-bit RSA encryption.
- Data Isolation. As a multitenant SaaS platform, we isolate data access for each tenant (customer). Customers can only view data on their managed infrastructure.
Data Access. OpsRamp provides different options to manage user identities.
- Customer Onboarding. Once a customer onboards into OpsRamp, we capture details of the organization, users and roles, hierarchy, permissions and contact details.
- Authentication. OpsRamp supports a standard user name password model, two factor authentication, single sign-on (Okta, OneLogin) or SAML based authentication (Active Directory Federation Services).
- Role Based Access Controls. We manage user access to devices and actions within OpsRamp with role based access controls. For example, Windows admins can only access Windows devices and Linux admins can only manage Linux servers.
- API Layer. OpsRamp provides a secure API interface with a unique token and secret for every authentication. API management stays with the administrator - you can create unique keys for every API level integration.
- PCI DSS. OpsRamp complies with the Payment Card Industry Data Security Standard (PCI DSS) to ensure your passwords are always secure. You can create password policy requirements in line with PCI DSS compliance.
Operational Controls and Processes
Availability. Customers can access their IT operations data anytime in our platform.
- Monitoring. We track system performance and availability across our infrastructure. SaaS Operations teams are immediately notified through alerts for any incidents.
- Data Centers. We have different PODs with strong redundancy. We work in active - active mode so that if one location fails, the other location immediately stands up.
- Service Level Agreement (SLA). We maintain a SLA commitment of 99.99% availability for our platform. You can access OpsRamp availability at http://status.opsramp.com/ which shows real-time status information of our services.
- Disaster Recovery. Automated backup systems perform scheduled backups of customer data. We have real-time two-way data replication across datacenters in each region.
Confidentiality. Customer data in OpsRamp is accessible to the right people at the tenant level.
- Data Transfer. We encrypt and transfer all data collected by OpsRamp using secure tunnels.
- Data Isolation. We isolate customer data at the tenant level and user role level.
- Data Access. We provide access to customer data after authentication of role based access controls.
Integrity. We ensure customer data stored in our platform is complete, valid, accurate, and authorized.
- Data Consistency. We restrict the ability to make changes in customer environments to authorized employees and on least privilege basis.
- Operational Security. We capture all access to our infrastructure using OpsRamp audit recordings. We govern all changes to infrastructure through a Change Advisory Board.
We've made strategic investments in people, policies, tools, and infrastructure for the highest levels of customer data security. Our security controls have helped us achieve rigorous industry standards like SOC 2 Type II and prove our commitment to SaaS security.