How Do You Keep Your Organization From Becoming The Next Target?
When it comes to high profile security incidents, we've had quite an eventful ride over the last few years. Security breaches at leading organizations have damaged corporate credibility, delivered huge financial losses, and resulted in massive litigation. Here's a quick behind-the-scenes analysis of three recent security breaches:
 |
||
| Name of Attack: WannaCry |
Date of Discovery: March 2017 |
Start Date of Attack: May 2017 |
|
Description: |
||
|
Patch Release Date: |
||
|
Impact: |
||
 |
||
| Name of Attack: Equifax |
Date of Discovery: December 2016 |
Start Date of Attack: March 2017 |
|
Description: |
||
|
Patch Release Date: |
||
|
Impact: |
||
 |
||
| Name of Attack: Heartbleed |
Date of Discovery: April 2012 |
Start Date of Attack: April 2014 |
|
Description: |
||
|
Patch Release Date: |
||
|
Impact: |
||
So, what conclusions can we draw from the three incidents? There are a few common patterns across these security breaches:
- The Consequences Aren't Pretty: You'll face financial, reputational, and productivity losses in the wake of a security breach. Did you know that the CEO, CIO, and CSO all had to resign from Equifax after a public outcry?
- It's Not Rocket Science: While security breaches can have sophisticated social engineering aspects, the underlying technical exploits are not exactly earth-shattering. Most incidents involve the discovery of a security flaw and the vendor releasing a patch quickly, but IT teams failing to apply the patches in time.
- IT Teams: It's Time To Accept Responsibility: While vendors are often blamed for security breaches, the onus for most incidents lies with enterprise IT teams. Technology vendors have quickly patched security flaws but enterprises have taken way too long to roll out patches.
Enterprise Patch Compliance: A Recurring Nightmare?
If you don’t want to make headline news, you’ll need to ensure that your operating systems and applications are up-to-date with the latest patches. Research shows that 80% of breaches occur due to "patches pending for more than 10 days and even up to a year." While the solution seems simple (buy a patching tool), it is no easy task installing the latest patches for an urgent security vulnerability. Here’s why simply investing in a patch management tool will not address growing security threats:
- Asset Discovery: Organizations often do not know what IT assets they have, or the location of their assets. Asset Discovery has gotten much more complex with the adoption of cloud-native (multi-cloud, containers, microservices, and serverless) architectures for digital services.
- Tools Disconnect: Let’s assume your organization has solved the asset discovery problem. Unfortunately, that’s just one piece of the puzzle. Most patching tools are disconnected from the asset discovery database. Integrations increase complexity and need careful analysis to understand which patches to apply urgently.
- Operational Visibility: Patching tools don’t play well with existing workflows, approvals, and processes. These tools are often managed by specialized teams, whose actions are not well understood by broader IT operations and security organizations.
- Complex Deployments: Patching tools are often complex to install, maintain, and integrate into your existing IT operations. You'll need to invest in skilled resources for enterprise-scale patch management.
- Yet Another Agent, Yet Another Tool: Patching tools require their own agents for patch scans and rollouts. You'll need to install and maintain specialized agents, which adds to the operational overhead.
The hand holding for patching tools can cause you to lose sight of patch compliance status. You'll need scalable patch management processes to keep pace with hybrid workloads that cut across on-prem, cloud, or both.
Gain Control Of Your Patch Management Landscape With OpsRamp
While OpsRamp is not a standalone security solution, we address common patching challenges so that your infrastructure is safe and protected at all times. Here’s how we offer a more scalable approach to patch and vulnerability management:
- Unified Asset Discovery: OpsRamp’s Unified Service Discovery delivers a complete picture of your Windows and Linux servers across datacenters, private clouds, and public clouds. You’ll see the what, where, and how of your infrastructure like never before.
- On-Demand Patch Scans: As soon as you onboard a server, our policies scans servers for missing patch updates. Drive real-time visibility for patch compliance levels and mitigate risk with the right processes.
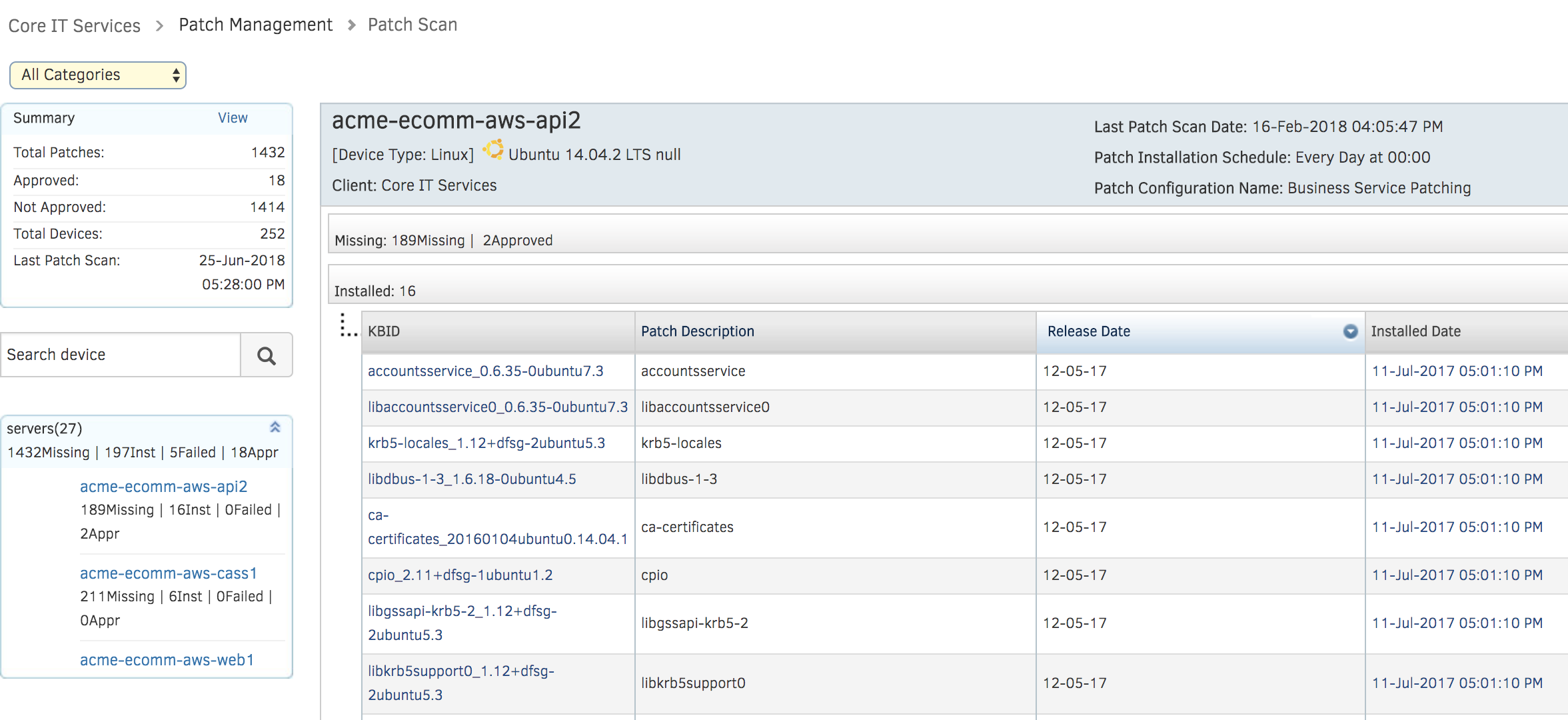
Figure 1- Understand the state of enterprise patch compliance with OpsRamp - Single Agent Footprint: OpsRamp employs a single agent for common operational processes such as discovery, monitoring, patching, and automation across your hybrid workloads. You’ll not need specialized agents for a single operational task anymore.
- Integrated Workflows: As a comprehensive IT operations management platform, OpsRamp serves as a collaboration venue for different teams. We connect asset discovery data to patching workflows so that you don't have to worry about missing patches for critical IT systems.
- Effortless Deployment: Since OpsRamp discovers your IT assets and scans for patches immediately, you can apply missing patch updates without manual intervention. Reduce manual oversight and simplify patch compliance processes with OpsRamp's auto-remediation policies.
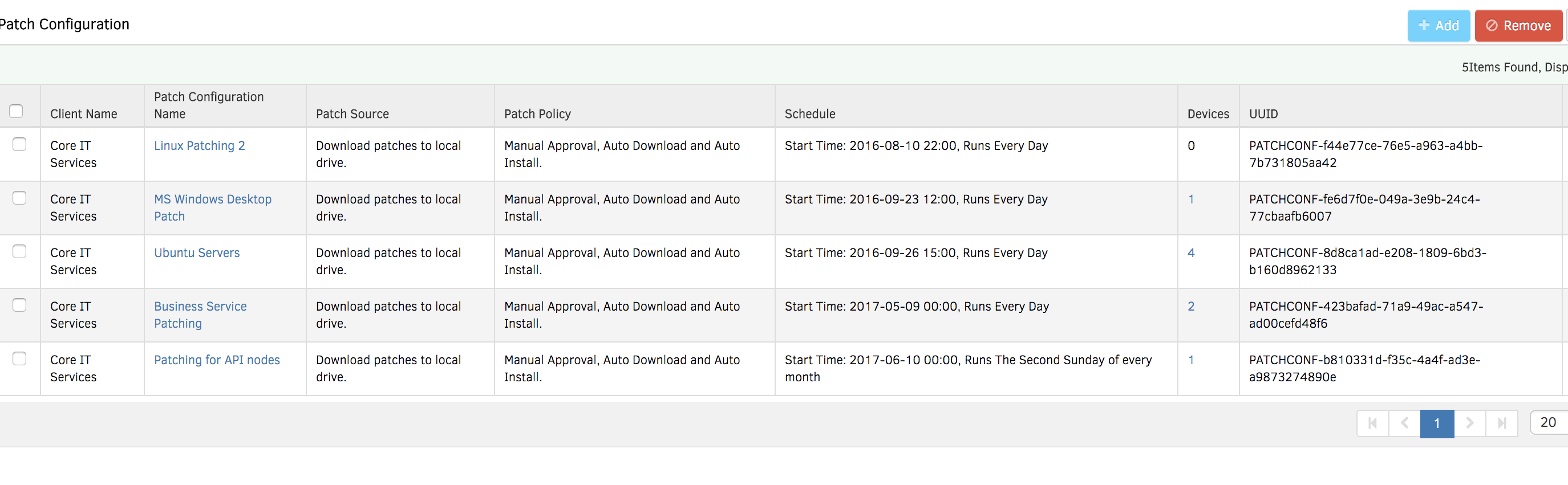
Figure 2 - Deploy missing patches without heavy lifting or manual processes
Next Steps:
- Learn more about our configuration management capabilities.
- If you would like to embrace consistent and repeatable patch compliance processes, talk to an OpsRamp solution consultant today.






